Qubes is an open source operating system based on Linux, which is designed to provide strong security for desktop computing. Its unique selling point is that all applications that are run on Qubes is sand-boxed from each other.
This is achieved by way of virtualization of all applications using Xen Hypervisor.
Computer systems usually provide OS security in three basic ways, namely –
- Security by correctness,
- Security by obscurity, and
- Security by isolation.
Qubes OS developers have embraced the path of security by isolation. To do this Qubes utilizes virtualization technology to isolate various programs from each other. This makes Qubes OS a secure by default operating system.
The idea is that virtual machines will be created on demand, for each application and discarded after use. Industry pundits have coined a new name for it – Disposable Virtual Machine technology.
The project is still in alpha stage and Invisible Things Lab – the firm behind this open source project aims to release a beta version of QubesOS some time this year (2010).
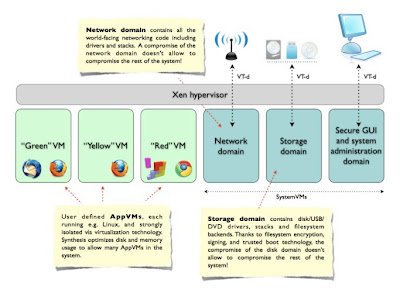
The GUI virtualization subsystem design of Qubes OS hinges on two primary goals, that being – security and performance. The sandboxing of applications in individual VMs provide security. For improving performance, Qubes OS architecture optimizes disk usage so that it is possible to run many VMs in the system without wasting precious disk resources.
The virtual machines (VM) that run in Qubes OS can be divided into two broad categories – AppVMs and SystemVMs.
AppVMs are the virtual machines used to host user applications such as email clients, word processors, web browsers and so on.
And those virtual machines that provide system wide services like networking, disk storage etc are classified as SystemVMs.
Qubes supports secure copy-and-paste and file sharing between applications across different AppVMs using Xen shared memory.
Qubes architecture has been designed by Joanna Rutkowska and Rafal Wojtczuk and funded by Invisible Things Lab.